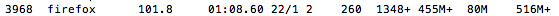Attack of the lol's - How to crash Tamper Data with a POST request tamper
So today at work I was working with a number of things looking for some bugs/exploits in web applications. Throughout my day I found a buggy upload form, and as a part of this decided to test the upload form with a large upload request (large file) which naturally would be submitted through a post request. So during my testing I run Backtrack 5 linux, and I have the “Tamper Data” plugin installed in Firefox in order to edit http header requests on the fly. So through my testing I just decided a quick way to generate a file of a fixed size of my choosing would be to do something like this:
perl -e ‘print “lol”x1000000;’ > test.txt
This output a file around 30MB due to ASCII characters being 1 byte long and having 1000000 lol’s makes 30 000 000 bytes, anyways….
So this file caused me some trouble, actually it crashes “Tamper Data” every time it is submitted. The reason being is that the POST request being sent contains the 10 000 000 lol’s in plaint text format and this seems to be too much for it to handle in the POST based tamper screen.
So I wanted to test this on OSX and these are the results:
Firefox goes to 100% CPU (from top in terminal):
Firefox gives a warning that the script is unresponsive:
Naturally I hit “Stop Script”, and I am presented with this:
Tamper Data just stays there even though the buggy script was stopped running! So then I’m like, well alright I’ll just close Firefox right? I close all of my open windows, but uhh nope? I can’t exit Tamper Data. Not even right clicking from the Dock and clicking on Quit. I’m just stuck with this:
At this point firefox is at normal CPU again, and I can open windows and it is fully responsive. Interesting though, I’ll probably report the bug. Not really a big deal, just for the “lols”.
~Josh